Fast, Accurate, Disassembly
Binary analysis is hard, but Doppler's core analysis algorithms reliably place you exactly where you need to be, when you need to be there.
- Most common binary formats and architectures supported.
- Analysis 'pass' concept.
- Navigable and interactive assembly.
- Save and share results and annotations.
- Binary Formats
- CPU Architectures
- Interactive Assembly Navigation
- Collaboration
- Reconfigurable Analysis Blocks



Scriptable API
Script any aspect of binary analysis. We eat our own dogfood here, as the GUI presents every bit of information using the same API available to you for automation.
- Automate access to anything you see in the frontend, and more...
- Extensible frontend annotation.
- Extensible backend components including binary format parsers, CPUs and analysis passes.
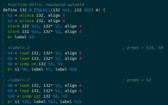
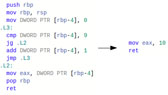
C/C++ Decompilation
Let's face it, often it is just easier and quicker to lift up the machine code being analyzed into a high level language. It doesn't get any better than Doppler's decompiler.
- Automated Lifting to LLVM IR.
- Control and Data Flow Passes.
- Abstract Syntax Trees (ASTs) Simplification.
- Interactive Source Code Navigation.
- Lifting to LLVM
- Control and Data Flow Passes
- Simplifying Abstract Syntax Trees (ASTs)
- Interactive Source Code Navigation


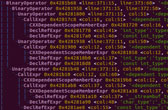
Enhanced Context through Function Naming
The single most time-saving commodity in reversing is to provide meaningful function names. Doppler names functions using a huge database of function signatures.
- Compiler Runtime Function Names.
- 3rd-Party Library Function Names
- Malware Function Names.
Large File Support
Reversing huge applications? No problem! We were frustrated with other tools grinding to a hault. Great care was taken to provide streamlined experiences on huge files.
- Doppler uses time and memory efficient machine code representations.
- Analysis of complex real-world applications is where Doppler shines.